How To Protect Your Wi-Fi Against Hackers?
There are many valid reasons why you need a protected Wi-Fi. When someone else is using your Wi-Fi, any illegal or suspicious activity done using your internet connection would mean trouble for you. Therefore, you need to be very careful not to allow anyone to use your Wi-Fi. Here are some useful tips to keep in mind and steps to do which would help you ensure greater safety against Wi-Fi.We provide you the best IT support services in Dubai
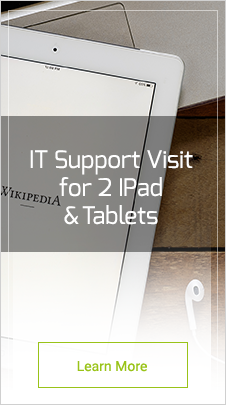
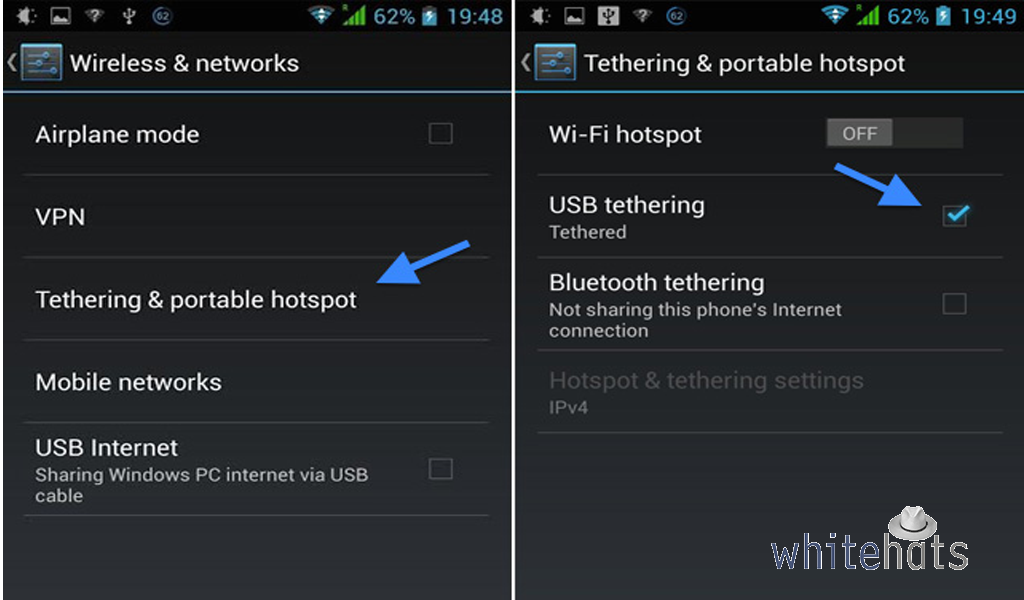 Tether Internet Connection
Tether Internet Connection
Many a times, we have the option to use our own mobile network for accessing internet. This kind of Wi-Fi connection is established privately, not accessible to other mobile phones. This means that you will be safely browsing the internet without any difficulties. However, you must check for the prices because data packages are significantly differently priced in various parts of the world. And the other drawback is that it drains away your smartphone’s battery.
 Use Encryption
Use Encryption
The usual way of sending and receiving data is through radio waves. One way of doing that data exchange is by using the encryption technology. When you encrypt the data that you are sending or receiving, it makes the information a lot safer. Many websites already deploy https technology which ensures a unique handshake with the service; in that case you have an already reduced risk of getting your information leaked. However, if you are accessing a website that does not provide that kind of facility, you may like to use encryption facility provided by your smartphone.
Proactively Look for Suspicious ActivityYou must also be vigilant about your Wi-Fi being used by others. When you are browsing internet, you must browse safely and do not go to websites that look suspicious to you. You can also block cookies or remove tracking in order to become safe. However, when you remove cookies, you will not be able to get a personalized website viewing experience. Do not install free software that does not look OK to you. When you do not know about the publisher of the software, there is probably something fishy going on and you need to avoid installing it.
Use Two Factor Authentication PasswordsOne other way of authenticating Wifi protections is by using VPNs with two factor authentication. This helps businesses protect information of sensitive nature. Many times, personal information is also protected using the same method. This combo with VPN makes it very difficult for hackers to hack into your Wi-Fi.
 Some Common Attacks on Wi-Fi
Man In The Middle
Some Common Attacks on Wi-Fi
Man In The Middle
Man In The Middle (MITM) is one of the most ways of attacking the Wi-Fi. The hackers are continuously monitoring the data that you are exchanging on your device. In this kind of attack, the hackers are continuously monitoring the data. And whenever they see an opportunity, the intercept and change the communication taking place. This is one of the most common ways of hijacking your Wi-Fi internet connection.
The Evil TwinThe Evil Twin is somewhat an advanced version of MITM with a slight variation. In this kind of attack, the hackers use a rogue Wi-Fi hotspot. The Wi-Fi that may seem to be very harmless can actually be very dangerous. You must be very cautious about free or public internet Wi-Fi connections available. Many hackers use that information to create a lot of problems for the device owners. As soon as you are connected to this rogue Wi-Fi, the hackers are given the access to view all the data being transferred using this kind of internet connection.
ConclusionThese are some of the most important tips to help you protect against Wi-Fi hacking. In order to make sure that you remain safe from these kinds of hacking attempts, you must be vigilant at all times. These simple tips would help you protect yourself and also ensure that your confidential information remains safe.